Encryption is widely used for security purposes because it prevents unauthorized third parties from accessing and disseminating private data. Backups are no exception and are often a target of data breaches. As part of a data protection strategy, you can implement encryption as an additional layer of security for your backups.
In this blog post, we cover how backup encryption can help you protect data in case of cyberattacks and improve the overall level of data protection for a more secure backup infrastructure.
What Is Backup Encryption?
Backup encryption is the process of converting backup data from a readable format to a secure format that is unreadable without a special decryption key or password. This ensures that even if the backup data is accessed by unauthorized individuals, it cannot be read, used, or exposed without the appropriate credentials, which are only available to authorized users. Backup encryption is a key security measure to protect sensitive information from theft, loss, or exposure during storage and transfer.
An example of encryption is converting plain text that is readable to everyone into ciphered data (cipher text in this case), which is unreadable if opened in the usual way without a cipher. As a result, after converting the original data using a secret code, the true meaning of this data is distorted and not understandable without a decryption key.
Importance of Encrypting Backups
Backup encryption is important to prevent data theft and breaches by unauthorized third parties. Cybercriminals can steal your data and sell this data to competitors or publish the stolen data on the internet to cause more damage to your organization. It can lead to significant reputational and financial loss.
Modern viruses, spyware, and ransomware are popular tools used by bad actors to implement their bad intentions, and their attacks have become more sophisticated and frequent. In addition to data protection purposes for avoiding unauthorized access, there are also other reasons why backup encryption is important. These include:
- Compliance and regulations. Some categories of businesses must meet certain regulatory requirements, such as the EU’s General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), California Consumer Privacy Act (CCPA), Health Insurance Portability and Accountability Act (HIPAA), Reporting for Critical Infrastructure Act (CIRCIA), SOC 3 (System and Organization Controls 3), etc. These regulation standards impose data encryption on organizations during storage and transfers.
- Improving overall security. Encrypted backups add a layer to security and improve the data protection strategy. Storing backups in an encrypted format makes it more secure to transport backup data on removable storage media such as hard disk drives to another location (for example, a disaster recovery site located in another geographic region). If a portable media with encrypted backups is lost or stolen, a third party cannot access critical and sensitive data.
Encrypted Backups against Ransomware
Backups are used to protect data by creating at least one additional copy of the original data to enable quick recovery when needed. Hence, if the original copy of data is corrupted or deleted by ransomware, then you can recover data from a backup. Attackers know this strategy and try to access data backups to destroy them as well to make data recovery impossible. Before corrupting or destroying backups, cyberattackers can copy backups to their servers to extract your data from stolen backups.
If backups are stored as encrypted files, this approach doesn’t help to protect these files from being corrupted or deleted by ransomware. Ransomware usually uses strong encryption algorithms to encrypt data and, thereby, make this data unreadable or, in other words, corrupted. Ransomware can re-encrypt backup files previously encrypted by you or your backup application to make them inaccessible to you.
At the same time, if ransomware sends your encrypted backup files to attack initiators, the attackers will not be able to access your data if strong encryption algorithms are used and keys, passwords, and credentials are stored in a safe place. Attackers like to demand ransom for not publishing the stolen data, but if you encrypt your backups and backup data is not accessible to attackers, the stolen encrypted backup data is useless for them. Encrypted backups are more resistant to tampering.
Hardware encryption can be more effective in some cases when it comes to ransomware attacks, but this approach has its own disadvantages. Hardware security modules (HSMs) can be used for hardware encryption. It can be a PCIe card and encryption keys can be stored on a special USB device (visually similar to a USB flash drive). Smart cards or HASP keys are other examples of storing hardware keys for encryption/decryption. It is more difficult to extract keys from such devices. The appropriate drivers must be installed on a computer in this case.
Use air-gapped storage to protect your backups against ransomware. This storage type prevents data modification by ransomware. Ransomware cannot copy data from air-gapped storage that is physically disconnected from a computer and network. Use immutable storage or storage with backup immutability capability, which purpose is similar to that of air-gapped storage for backup protection.
Encryption at Rest and in Transit
Backups can be encrypted while being written to the destination storage media. As backed-up data is usually transferred over the network before being written on the destination storage, it is important to encrypt the network traffic with this data. Bad actors can use a traffic sniffer to intercept (capture) the network traffic and access backup data in this way. Encrypting data in transit reduces the risk of such an event. Encryption in transit is performed between the data source and backup destination storage.
Encryption at rest involves encrypting backup data on backup storage such as a backup repository on hard disk drives, tape cartridges, cloud, etc. While encryption of backed-up data in transit protects this data if hackers access a network, encryption of backups at rest protects them if hackers access backup storage.
Both encryption in transit and encryption at rest can be used together for backup encryption and increasing the security level.
Encryption Algorithms
Complex mathematical algorithms and encryption/decryption keys are used to implement data encryption. For more convenience, software can transform a password or passphrase into an encryption key of the appropriate length. This approach allows users to memorize their passwords, which is easier than learning long encryption keys. The efficiency of encryption for backups, similarly to other data, depends on the encryption algorithm.
There are symmetric and asymmetric encryption algorithms. In symmetric algorithms, one key is used to encrypt and decrypt data. In asymmetric algorithms, a key pair is used: a public key to encrypt data and a private key to decrypt data.
Examples of both include:
- Symmetric cryptographic algorithms are AES, DES, 3DES, Blowfish, Twofish, and others.
- Asymmetric cryptographic algorithms are RSA (1024, 2048, and 4096-bit), ECC, DSA, Diffie-Hellman, and others.
Advanced Encryption Standard (AES) is one of the most used encryption algorithms nowadays due to its high level of security. The key length is important and defines how long the encrypted data can be considered as secured and protected. A 128-bit key should be enough to protect data for up to three years. Longer supported keys are 192-bit and 256-bit keys.
AES-256 ensures the highest level of security with a 256-bit key length. Thousands of years are required to brute force an AES-256 decryption key (taking into account the maximum performance of modern computers). The US government has been using AES to protect data since 2003. This cryptographic algorithm was well-tested and approved by cryptography experts.
Network transactions using Secure Sockets Layer/Transport Layer Security (SSL/TLS) are encrypted in transit. The most common example is the HTTPS protocol. TLS 1.1 or higher should be used for strong encryption.
Longer cryptographic keys ensure a higher level of security but require more CPU resources for data encryption. It also takes more time to recover data from encrypted backups. When it comes to data encryption during transfers over the network, then with a longer encryption key the transfer speed for useful data is also lower. This is due to:
- Encrypted data can sometimes be slightly larger due to the padding added to ensure the data aligns with the block size of the encryption algorithm.
- Encrypted connections often include additional metadata and headers for managing the encryption process. This includes elements such as certificates, encryption keys and handshaking information.
- These extra bytes of metadata contribute to a larger data payload, slightly increasing the amount of data that needs to be transmitted.
- The increase in data size can reduce effective network throughput as more data is being transmitted for the same amount of original information.
Encryption algorithms can be classified based on the input type as stream cipher and block cipher for symmetric algorithms. In stream ciphers, one block is encrypted at a time. Block ciphers are a type of symmetric key encryption algorithm that:
- A block cipher encrypts data in fixed-size blocks (for example, 64-bit or 128-bit blocks).
- A block cipher uses a symmetric key, meaning the same key is used for both encryption and decryption.
- Common block cipher algorithms include AES, DES, and Blowfish.
Encryption vs. hash
A hash function is an irreversible function that can transform a text string or another set of data into a hash. The calculated hash can then be used to check data integrity (files) and authenticity (password hashes), or generate unique identifiers (fingerprints). Examples of hash functions are SHA-256 and MD5.
Risks Associated with Encrypted Backups
Encrypted backups add more complexity and overhead to a backup subsystem. A lost key or password can cause serious problems because it will be impossible to recover data from an encrypted backup. If a third-party person or attackers access the encryption keys, data theft and data loss can occur. For these reasons, organizations should use a reliable strategy to store encryption keys for encrypted backups and manage these keys, key rotation schemes, and security policies to provide keys only for authorized users.
There are also risks related to encrypting tape cartridges with backups. LTO-4 to LTO-7 tape standards support AES-256 encryption of tape media. A symmetric encryption/decryption key is stored on a tape drive when this drive writes data on tape but no longer than that. These keys are not written to tape for security reasons. If a disaster damages the data center and backup servers are destroyed, issues of data recovery can occur because decryption keys are destroyed with them.
To reduce the risks, it is recommended that you perform backup testing regularly to ensure that data can be recovered from encrypted backups in different scenarios.
When using encryption on the hard disk drive level or full disk encryption, in case of an HDD failure, data recovery in a lab may not be possible. Backup copies help reduce the risk of storing backups on an encrypted HDD or SSD.
Key Management
There is a risk in using one key for the encryption of all data. If an attacker can get this key, then the attacker can decrypt and access all data. For high-security standards, it is recommended that organizations use multiple encryption keys for different sets of data. These keys should be stored in a safe place with access only for authorized users who have permissions. Administrators have to protect keys and ensure that the keys are available in case of a disaster.
To improve the process of key management during the entire lifecycle of encryption/decryption keys and to protect keys from loss and leakage, a key management system or KMS can be implemented. The KMS can be used to control who can access keys as well as how keys are assigned and rotated. One of the key management standards is the Key Management Interoperability Protocol (KMIP). Key vaults can be used to store and manage encryption keys.
Preparing for Backup Encryption in NAKIVO Backup & Replication
NAKIVO Backup & Replication is a data protection solution that supports encrypted backups and can encrypt backed-up data using the following approaches:
- Source-side encryption to encrypt data before it leaves the source, while it is transferred, and throughout its lifecycle in the backup repository
- Network encryption to encrypt data while in transit over the network to the backup repository
- Backup repository encryption to encrypt data while at rest in storage
The NAKIVO solution uses strong AES-256 encryption that is considered the industry standard for encrypting data worldwide.
Backup encryption at the source is available starting with version 11.0. The advantages of this feature is that backed-up data is encrypted first at the source side, and then this encrypted data is transferred to a backup repository and stored in the backup repository in encrypted form. This approach simplifies the configuration and backup processes and can be used for backups to the cloud as well.
System Requirements
Requirements for source-side encryption
In version 11.0 of NAKIVO Backup & Replication, a new option was introduced allowing you to configure backup encryption at the backup job level. The data is encrypted at the source and remains encrypted over the network and in storage in the backup repository.
Supported backup destination types:
- Local folder
- NFS and SMB share
- Amazon EC2
- Amazon S3 and S3-compatible object storage
- Wasabi
- Deduplication appliances
- Azure Blob storage
- Backblaze B2
- Tape
Supported backup repository type: Incremental with full
Requirements for network encryption
Two Transporters are required to configure network encryption for versions 10.11.2 and older. A Transporter is a core component of NAKIVO Backup & Replication responsible for data processing, transferring, encryption, compression, etc.
Encryption for transferring data over the network happens between the two Transporters: the Transporter at the source side compresses and encrypts the data before sending it to the destination Transporter, and the destination Transporter decrypts the data and writes it to a backup repository.
Requirements for backup repository encryption
Backup encryption in storage at the destination is available at the backup repository level when creating a backup repository in NAKIVO Backup & Replication.
Backup repository encryption is supported for the incremental with full and forever incremental backup repository types on Linux OS.
How to Enable Backup Encryption
Let’s explore how to enable different types of backup encryption in the NAKIVO data protection solution.
Source-side backup encryption (version 11.0 and higher)
In NAKIVO Backup & Replication v11.0, you can set backup encryption at the source for secure data transfers and storage. You can configure these options at the Options step of the backup or backup copy job wizard.
Source-side backup encryption means that data is encrypted before being sent to the repository, that is, at the source.
To enable source-side backup encryption at the backup job level in v11.0, do the following:
- In the Backup encryption drop-down menu, select Enabled.
- Click Settings at the Backup encryption line to set the password for encryption.
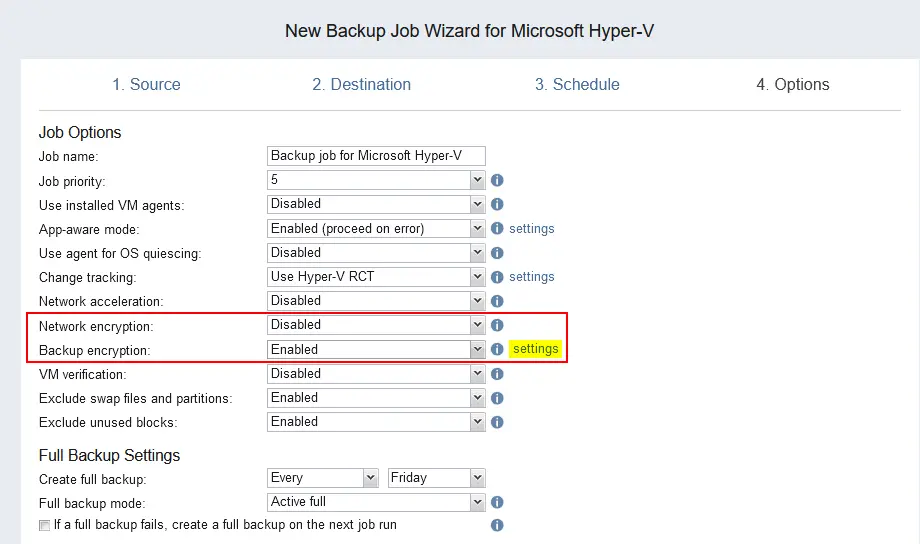
- Select Create password, enter a password, and confirm the password.
Enter a description for this password. The name entered in the description will be displayed in the list of passwords which you can select later for different backup jobs. We use Hyper-V Backup as the name for the password.
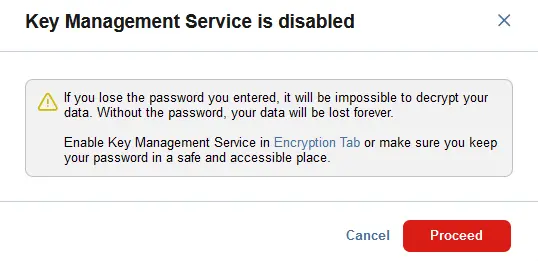
If you don’t use AWS KMS, then you will see the message: The Key Management Service is disabled. See Encryption Tab. If you have configured and enabled AWS KMS, this warning will not be displayed. Note, that to configure KMS to manage your passwords, you must add your AWS account to the NAKIVO Backup & Replication inventory first.
Click Proceed.
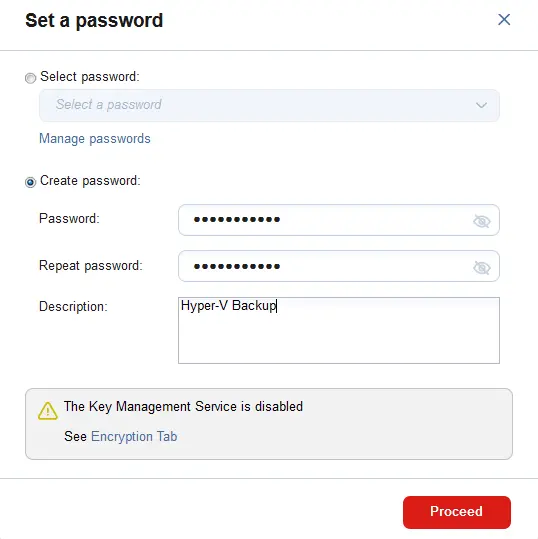
- The password you have entered is applied automatically.
Alternatively, you can select an existing password.
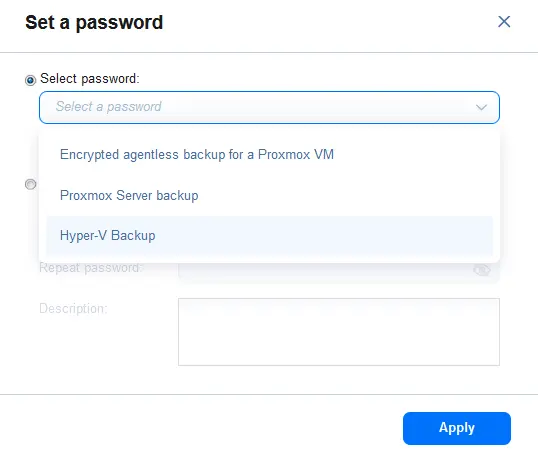
- Click Finish to save job settings or click Finish & Run to save settings and run the job with configured backup encryption.
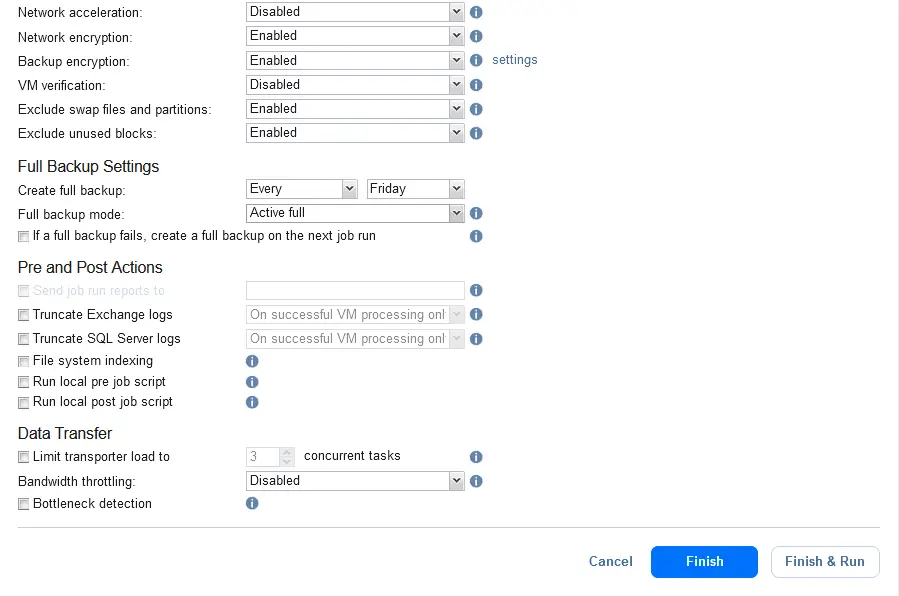
- When applying the job settings, you will see a warning that the backup is password-protected and if you lose the password, it will be impossible to decrypt the data. This warning is displayed if you have not enabled AWS Key Management Service. Click Proceed.
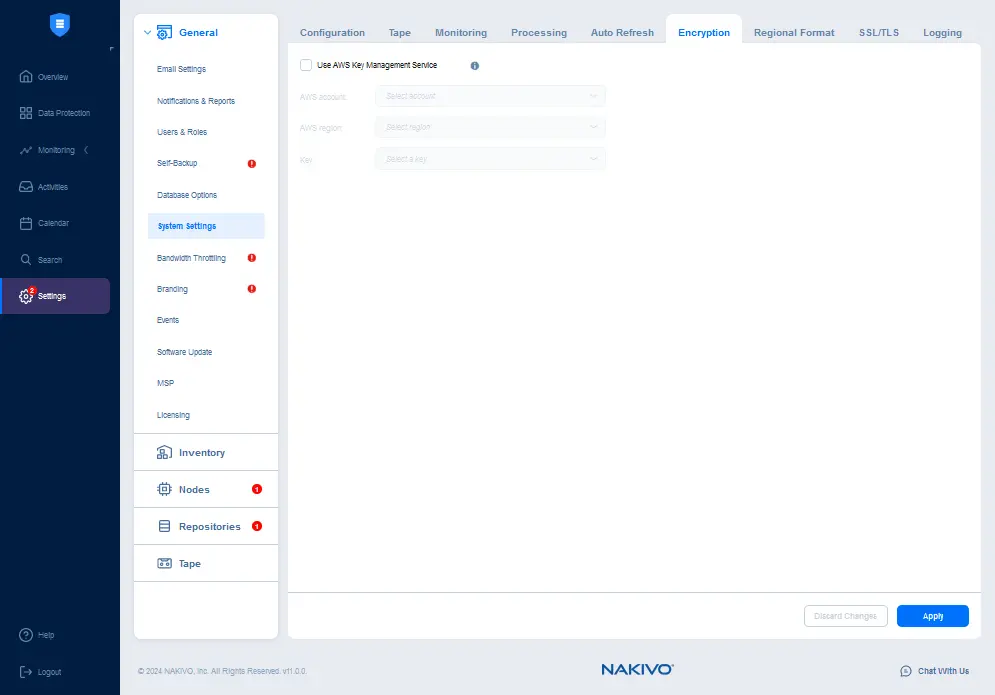
You can use the AWS Key Management Service to ensure that you don’t lose encryption passwords you set for backups. To use AWS KMS, in the web interface of NAKIVO Backup & Replication, go to Settings > General > System settings, select the Encryption tab, and select the Use AWS Key Management Service checkbox. Remember that you must add the AWS account to the NAKIVO Backup & Replication inventory first to enable AWS KMS.
Configuring network encryption for backups
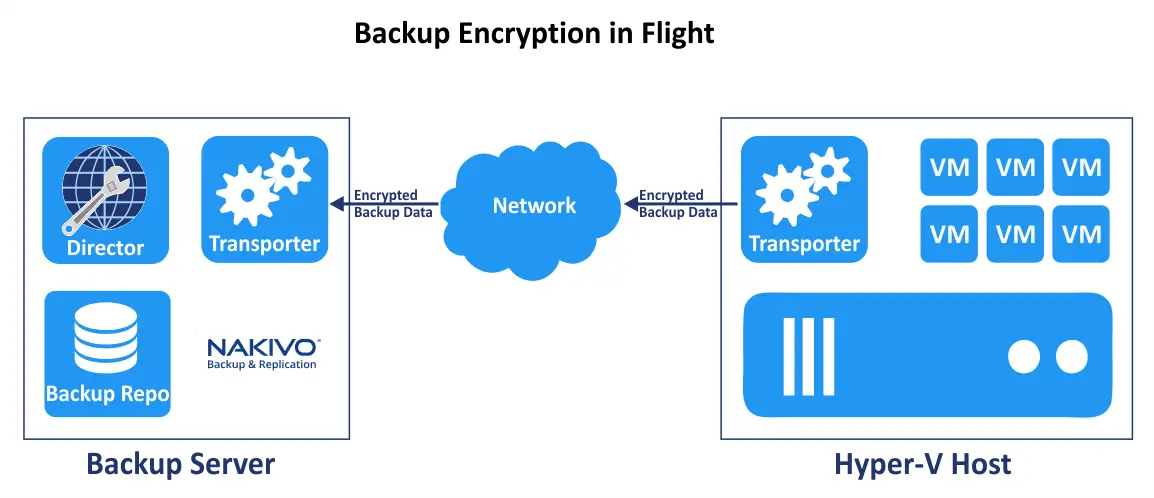
We can improve the security level and configure encryption for backup data while being transferred over the network. One of the main requirements for versions earlier than v10.11 for this feature to work is that two Transporters must be installed on different machines.
We can add a Hyper-V host to the inventory and back up a Hyper-V virtual machine using network encryption to an encrypted backup storage. When we add a Hyper-V host to the NAKIVO inventory from the web interface of the NAKIVO solution, a Transporter is installed on the Hyper-V host.
This configuration is visualized in the screenshot below.
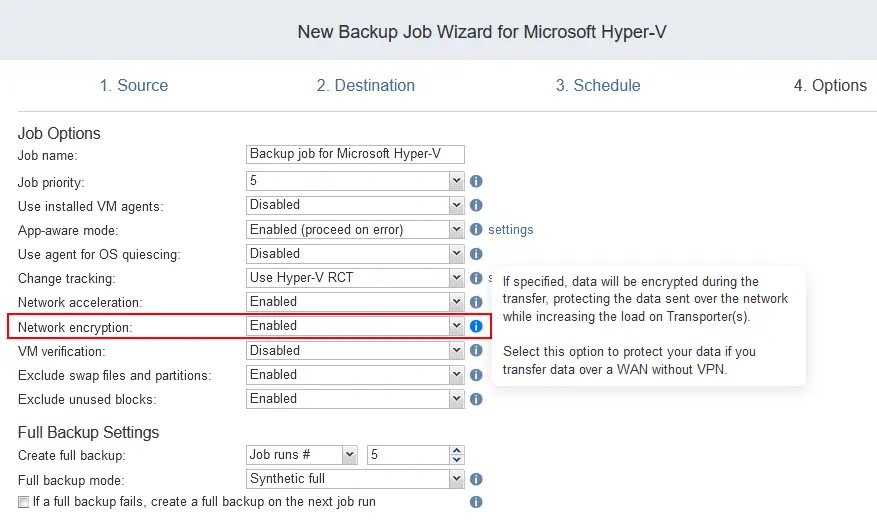
Now, we can configure network encryption for transferring backups over the network in backup job options. Enter a display name for the job and other parameters.
In the Network Encryption drop-down list, select Enabled. This parameter is active because two Transporters are used to transfer backup data between machines.
We can also deploy a Transporter on the remote machine that can be located on a local site to increase the number of processed workloads to back up. A Transporter can be deployed on a remote machine on a remote site to store backups and backup copies to implement the 3-2-1 backup rule. In this case, backup data transferred over the network can be encrypted and be protected against breaches even if you can’t use an encrypted VPN connection.
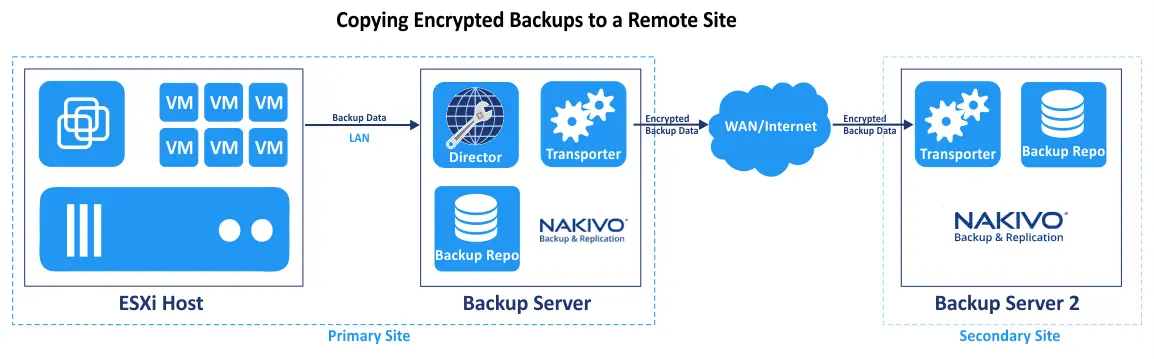
Enabling encryption for a backup repository
You can configure backup encryption for the entire repository when creating a backup repository. This feature has been available in NAKIVO Backup & Replication since v5.7. iIf you have previously created a backup repository without encryption, you need to create a new repository to enable encryption at the backup repository level. The Onboard Transporter has been installed by default. Let’s create a backup repository and focus on enabling backup encryption.
NOTE: Enabling encryption for the entire backup repository disables the immutability feature for backups stored in this repository. This feature is only available for backup repositories on Linux-based machines.
Encryption settings for the entire backup repository are configured at the Options step of a backup repository creation wizard:
- In the Encryption drop-down menu, select Enabled. Then the password fields appear below.
- Enter the encryption password and confirm this password.
- Hit Finish to finish creating an encrypted backup repository.
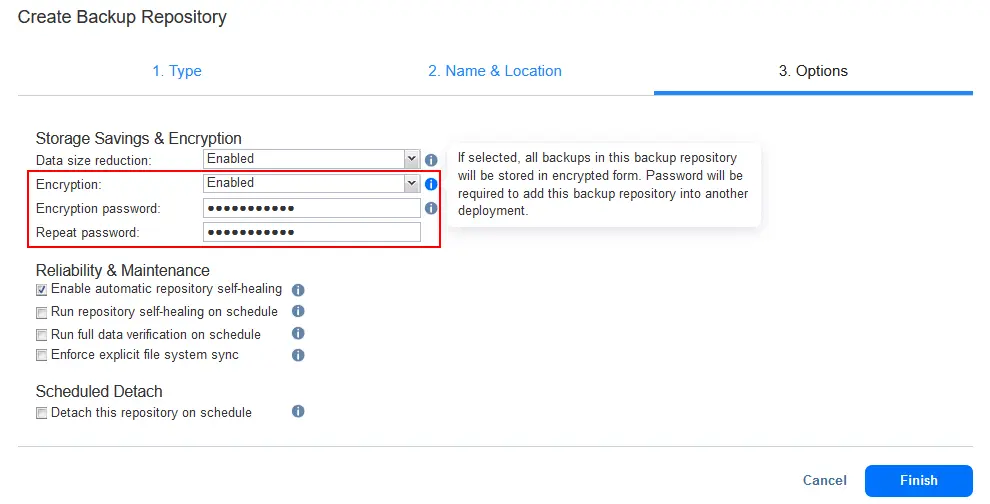
From now, all backups stored in this backup repository will be encrypted.
Recovery from Encrypted Backups
Recovery of data from encrypted backups is similar to unencrypted backups. If KMS is not enabled or if a repository is attached to a new NAKIVO solution instance, you have to provide passwords again in order to allow recovery. In other words, if you attach an encrypted backup repository to the instance of NAKIVO Backup & Replication (a different instance or a newly installed instance of the Director), you must enter the encryption password previously set for this backup repository (if you enabled encryption at the repository level).
If KMS was enabled while encrypting the backups after attaching a repository to a new NAKIVO solution instance, you only need to enable KMS again and select the appropriate key (which was used last time). In this case, you will not need to re-enter all the passwords.
Source:
https://www.nakivo.com/blog/how-to-enable-backup-encryption/













