Data backup is critical to data loss prevention and swift recovery. A part of a secure and resilient data protection strategy is backup encryption to prevent breaches and access to data by unauthorized persons. This blog post covers encryption types based on where data is encrypted and explains how a specific approach can be used for an effective backup encryption strategy.
Types of Backup Encryption
Encryption can be classified into different categories based on the encryption algorithm, key length, and the location where encryption is carried out. Source-side encryption and target-side encryption are terms used in the context of data encryption, particularly when data is being transferred between systems, such as in cloud storage or data backup scenarios. They refer to where the encryption and decryption processes occur.
Source-Side Encryption
Source-side encryption, also known as client-side encryption, involves encrypting data on the client’s (source) system before it is transmitted to another system, such as a cloud storage service or remote server. This process ensures that the data is protected from the moment it leaves the client’s control, maintaining its confidentiality and integrity throughout transmission and storage.
NOTE: Source-side encryption is closely related to what is often referred to as client-side encryption. In fact, the two terms are frequently used interchangeably, though the context can vary depending on the specific application or system in question.
How source-side encryption works
When a user or application generates data on a device, such as a computer or server, the data is first encrypted locally on that device. The encryption process uses a strong encryption algorithm, like AES (Advanced Encryption Standard), which transforms the readable data into an encrypted format that is unreadable without the corresponding decryption key. This encryption key is typically managed by the client, meaning that only the client – or authorized entities with access to the key — can decrypt and access the original data.
Once the data is encrypted, it is transmitted to the destination system. During this transmission, the data remains encrypted, reducing the risk of breaches if it is intercepted. Since the data is already encrypted before it leaves the client’s environment, the receiving system does not need to know its contents or be able to decrypt it.
After reaching the target system, the data is stored in its encrypted state. The server or storage service holds only the encrypted data and typically has no access to the decryption keys, meaning it cannot decrypt the data on its own. This setup ensures that the data remains secure even if the storage system is compromised, as the data cannot be read without the right decryption key.
When the client or an authorized user needs to access the stored data, the encrypted data is retrieved from the target system and returned to the client (source system). The client then uses the original decryption key to decrypt the data locally, converting it back into its original, readable form. This decryption process occurs entirely on the client’s system, ensuring that the data remains under the client’s control throughout its lifecycle.
Source-side encryption is especially valuable in scenarios where the client wants to maintain control over data security, such as when storing sensitive information in cloud environments. However, it also requires the client to manage encryption keys securely, as losing these keys would result in the data becoming permanently inaccessible. This approach provides a strong level of data protection.
Benefits of source-side encryption
Source-side encryption allows the client to maintain complete control over the encryption process, including the encryption keys. This approach ensures that data is protected before it leaves the client’s environment, providing a higher level of trust and autonomy. The client can tailor the encryption methods and key management strategies to meet specific security and compliance requirements, making this approach particularly beneficial for sensitive or regulated data.
Security
One of the main security benefits of source-side encryption is that the data is encrypted at its origin, meaning that it is secure during transit and at rest. Because the client controls the encryption keys, the data remains inaccessible to anyone, including service providers or third parties, who do not possess the keys. As a result, the risk of unauthorized access or data breaches is significantly reduced, even if the storage system is compromised. Additionally, the encryption is end-to-end, ensuring that the data remains protected throughout its entire lifecycle.
Performance
Source-side encryption can have a noticeable performance impact, as the encryption and decryption processes occur on the client’s (source) device. Depending on the size and complexity of the data, this can require significant computational resources, potentially slowing down operations, especially for large datasets or resource-constrained devices. Key management can also add complexity, requiring careful handling to avoid performance bottlenecks or potential data loss if keys are mishandled.
Target-Side Encryption
Target-side encryption, also known as server-side encryption, refers to the process of encrypting data by the target system (such as a cloud service provider, remote server, or database) after it has been received from the source (client). This encryption approach is widely used in cloud storage services, databases, and other scenarios where data needs to be protected after it is received and stored. This method places the responsibility for encrypting and securing the data on the server (target) rather than the client (source).
How target-side encryption works
When a client sends data to a target system, the data typically arrives in plain text, though it may be protected during transmission using transport-layer security protocols like TLS/SSL. Once the data reaches the target system, the server takes over the encryption process. The server uses a strong encryption algorithm, such as AES (Advanced Encryption Standard), to convert the data into an encrypted format. This ensures that the data is protected and unreadable to any users or applications that might gain unauthorized access to the server’s storage.
The target server manages the encryption keys necessary for this process. These keys may be generated and stored by the server itself, or they may be managed through a dedicated key management service (KMS). The encryption keys are crucial for both encrypting and decrypting the data and their management is central to maintaining the security of the encrypted data.
After encrypting the data, the target server stores it in its encrypted form, whether on disk, in a database, or within a cloud storage system. The data remains encrypted at rest, meaning that even if the physical storage medium is accessed by unauthorized individuals, they would only see the encrypted data, which would be useless without the decryption key.
When an authorized user or system requests the data, the server decrypts it before delivering it back to the client. This decryption process is typically not visible to the client, who may not even be aware that the data was encrypted during storage. The client receives the data in its original, readable form, ready for use.
Target-side encryption simplifies the process for the client (source side), as the client does not need to worry about handling encryption or managing keys. The server or cloud provider handles these responsibilities, ensuring that data is uniformly encrypted and protected according to the provider’s security policies. However, this also means that the client must trust the server to manage the encryption keys securely and to perform the encryption and decryption processes properly.
This method is commonly used in cloud storage services, databases and other environments where large amounts of data need to be stored securely. It provides an efficient way to protect data at rest, making it a popular choice for organizations that want to ensure data security without adding complexity to the client’s side of the operation.
Benefits of target-side encryption
Target-side encryption simplifies the encryption process for the client at the source side by shifting the responsibility to the target server or cloud provider. The client does not need to worry about implementing encryption algorithms or managing encryption keys, as these tasks are handled by the target system. This makes it easier to integrate encryption into existing workflows, particularly in environments where ease of use and scalability are important. It also ensures consistent application of encryption policies across all data stored on the server.
Security
While target-side encryption ensures that data is encrypted at rest, it requires the client to trust the server or cloud provider to manage the encryption process and protect the encryption keys. The security of the data depends on the server’s ability to properly manage keys and enforce security policies. However, if the server is compromised, there is a potential risk that unauthorized users could gain access to both the encrypted data and the keys needed to decrypt it. To mitigate this, many services offer additional security features, such as key management services (KMS) and hardware security modules (HSMs) to strengthen key protection.
Performance
Target-side encryption generally has a lower performance impact on the client (source side), as the heavy lifting of encryption and decryption is done by the target server. This can lead to better performance on the client side, particularly for devices with limited processing power. However, the encryption and decryption processes still consume resources on the server, which can impact the server’s performance, especially in high-demand environments. Additionally, the need to decrypt data on the server before sending it back to the client can introduce some latency, although this is often minimal in well-optimized systems.
Source-Side Encryption vs Target-Side Encryption
The table below lists the main parameters to summarize the differences between source-side encryption and target-side encryption (client-side encryption vs server-side encryption).
| Feature/Aspect | Source-Side Encryption | Target-Side Encryption |
| Definition | Data encryption is performed at the source before it is transmitted. | Data encryption is performed once it reaches its target destination. |
| Control | Typically, the data owner or sender has control over the encryption process and keys. | The data recipient or storage service provider usually manages the encryption process and keys. |
| Key management | Keys are usually controlled and managed by the data sender/owner. | Keys are managed by the data recipient or the storage service provider. |
| Security responsibility | Primary responsibility lies with the data sender to ensure data is encrypted before transmission. | Primary responsibility lies with the data recipient or storage provider to encrypt data upon receipt. |
| Transmission security | Data is encrypted during transit, providing security against interception. | Data could potentially be intercepted in plain text during transit if not encrypted; focuses more on protecting stored data. |
| Integration complexity | May require more integration work on the part of the data sender to implement encryption mechanisms. | Generally easier to implement since the encryption process happens post-receipt, often using standard service tools. |
| Performance impact | Potential performance overhead on the client side due to encryption processes before data is sent. | Less impact on the client side; performance overhead is on the server or storage side due to encryption processes upon receipt. |
| Compliance and policy | Allows senders to comply with specific data protection policies and regulations by controlling encryption themselves. | May satisfy compliance requirements related to data at rest encryption policies and responsibilities of the data custodian. |
| Use cases | Useful in scenarios where secure transmission is critical, such as sensitive data exchange. | Common in cloud storage and data warehousing solutions where data protection is needed primarily for stored data. |
Source-Side Backup Encryption with NAKIVO
Both source-side encryption and target-side encryption types can be used for data backup. Let’s explore source-side encryption in the context of data backup.
NAKIVO Backup & Replication is an advanced data protection solution that supports backup encryption. A strong AES-256 (the 256-bit length of the encryption key) algorithm is used for encryption in the NAKIVO solution. Encryption can be configured at the backup repository level (for all backups stored in a backup repository) as the target encryption. The other option is configuring encryption at the backup job level using source-side encryption. As a result, backups are encrypted during transfers and stored as encrypted data in the backup repository.
Source-side backup encryption requires entering a password. A strong hash generated based on the provided password is used to create the encryption/decryption key. It is important not to lose the encryption password, as you won’t be able to restore data from the encrypted backup without the password.
Requirements for source-side encryption:
- NAKIVO Backup & Replication v11.0 or newer
- Data storage type: Incremental with full backup (tape is also supported)
Configuring source-side encryption
Source-side encryption for backups is configured in the web interface at the job level.
- Go to the Options step of a backup job wizard in NAKIVO Backup & Replication to set encryption options.
- Set the Backup encryption option to Enabled to implement source-side encryption for a backup.
NOTE: When network encryption is enabled, the backed up data is encrypted before being transferred over the network and decrypted when being written to the destination backup repository. The load of Transporters is increased for encrypting and decrypting data. When backup encryption is enabled, data is encrypted at the source side, is transferred as encrypted data, and stored as encrypted data in the backup repository. Enabling both backup encryption and network encryption increases the load for double encryption of data and is not necessary.
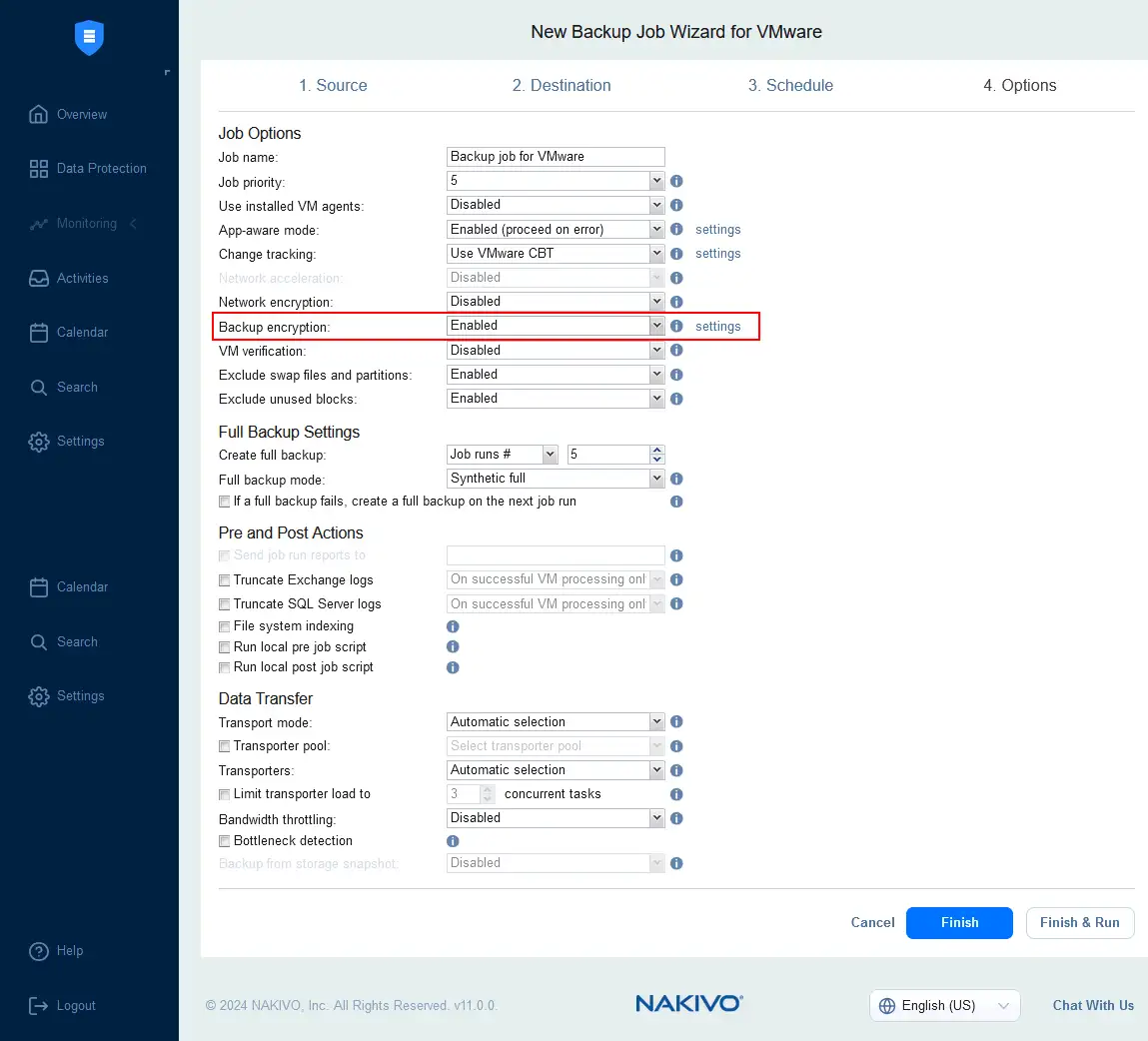
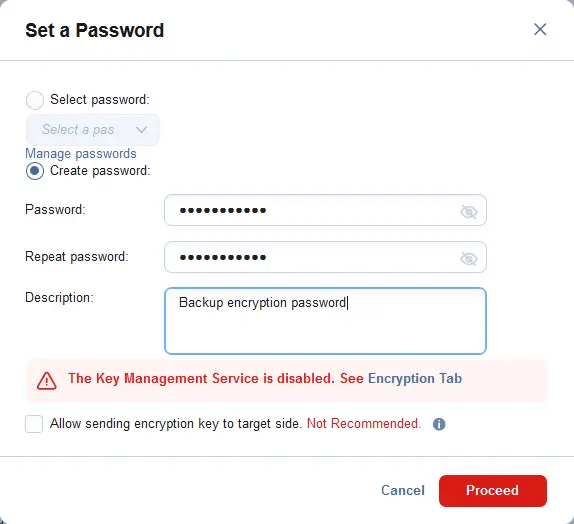
- Click Settings to set an encryption key.
- Set the needed parameters in the Set a Password window.
- Create a new password and confirm the password.
- Enter a description, for example, Backup encryption password.
When you hit Proceed, the new password is saved to a database of the NAKIVO Director, and you can later select this password for other backup jobs.
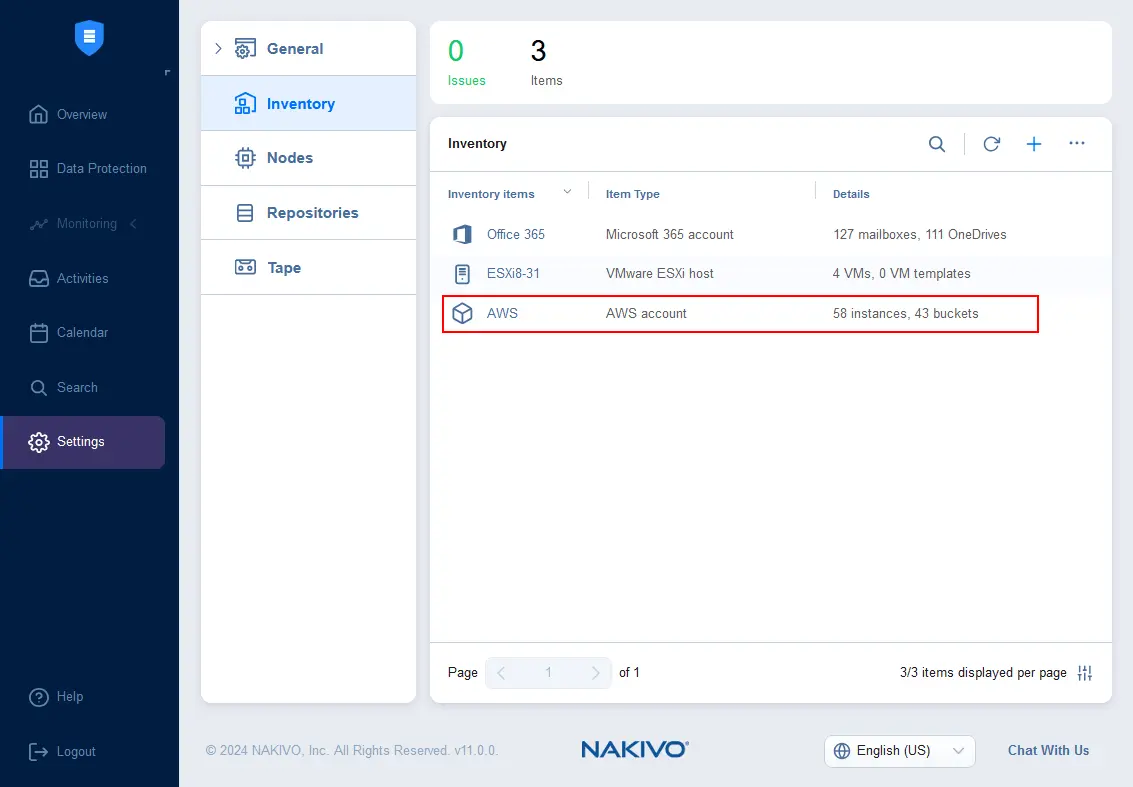
You can also set up a Key Management Service (KMS) for additional protection measures. NAKIVO Backup & Replication supports AWS KMS.
- To enable AWS KMS, you need to add an AWS account to the NAKIVO inventory.
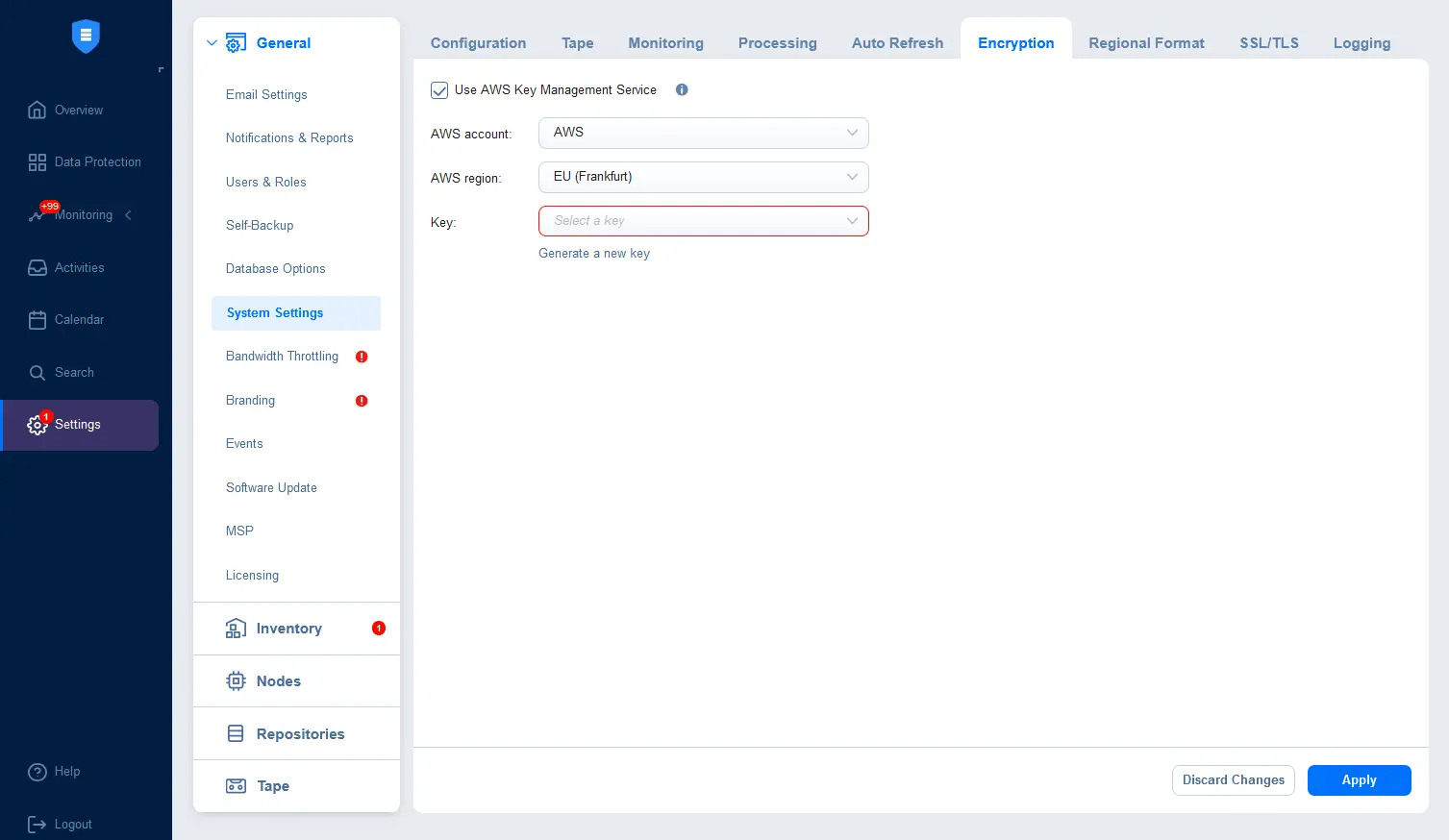
- To enable the AWS Key Management Service for backup encryption, go to Settings > General > System Settings and switch to the Encryption tab.
- Select the Use AWS Key Management Service checkbox.
- Select an AWS account added to the NAKIVO inventory.
- Select an AWS region.
- Select a key.
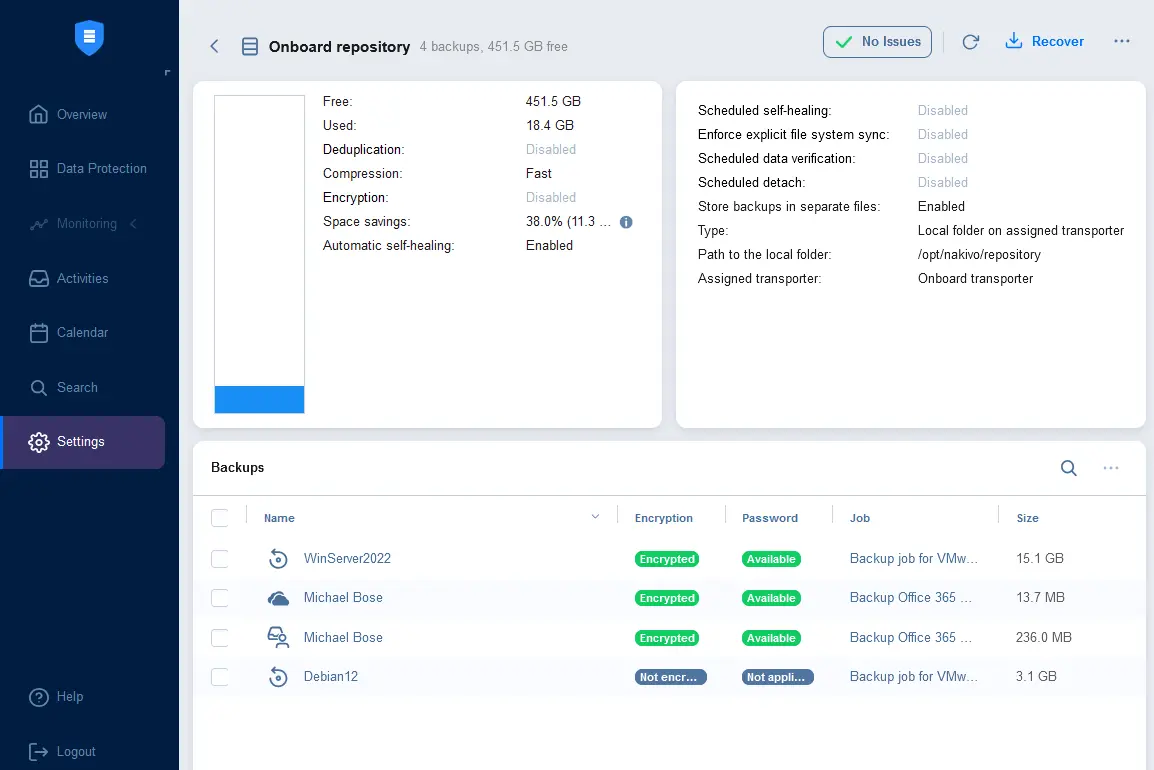
You can check the encryption status by going to Settings > Repositories and selecting a backup repository (for example, the Onboard repository). Click the repository name to see the list of backups in this repository.
This page displays the backup name, encryption status, encryption password status, job name, and size.
Backup encryption status:
- Encrypted
- Not encrypted
Encryption password status:
- Available – a corresponding password hash is saved in the NAKIVO Director’s database.
- Not available – a backup (recovery point) is encrypted, but the encryption password hash is not available in the Director’s database.
- Not applicable – is displayed if a recovery point of a backup is not encrypted.
You can edit backup job options at any time and change backup encryption settings.
Conclusion
Source-side encryption is a secure and effective measure to protect backed-up data when transferring it over the network and storing it in a target backup repository. This type of backup encryption is effective for different scenarios, including a local backup and a backup to the public cloud. Using passwords to generate encryption keys is affordable and friendly for users. Moreover, the advanced Key Management Service, such as AWS KMS, can be used to avoid forgetting and losing the encryption keys.
Download the latest version of NAKIVO Backup & Replication which supports source-side encryption and target-side encryption to effectively implement your backup strategy.
Source:
https://www.nakivo.com/blog/backup-encryption-options/













